How to register the documenter tool as a Microsoft Entra ID application
To connect to an Azure database with the Microsoft Entra MFA authentication, you should register dbForge Documenter for SQL Server as a Microsoft Entra ID application and set permissions. During the registration, an application ID will be generated automatically.
Registering dbForge Documenter for SQL Server as a Microsoft Entra ID application
1. Sign in to the Azure portal.
2. In Azure services, click Microsoft Entra ID. Then, select Add > App registration.
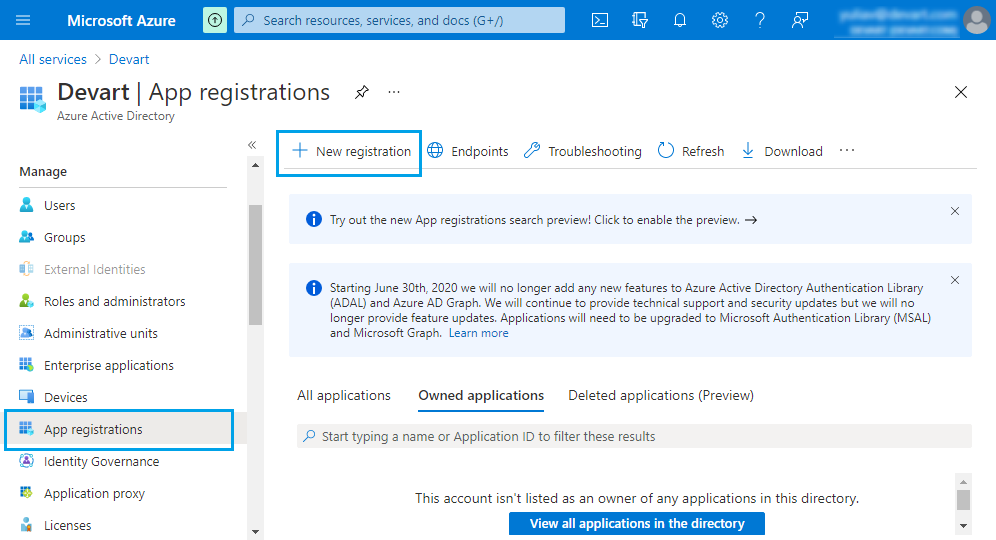
3. On the Register an application page, enter dbForge Documenter in the Name field and click Register.
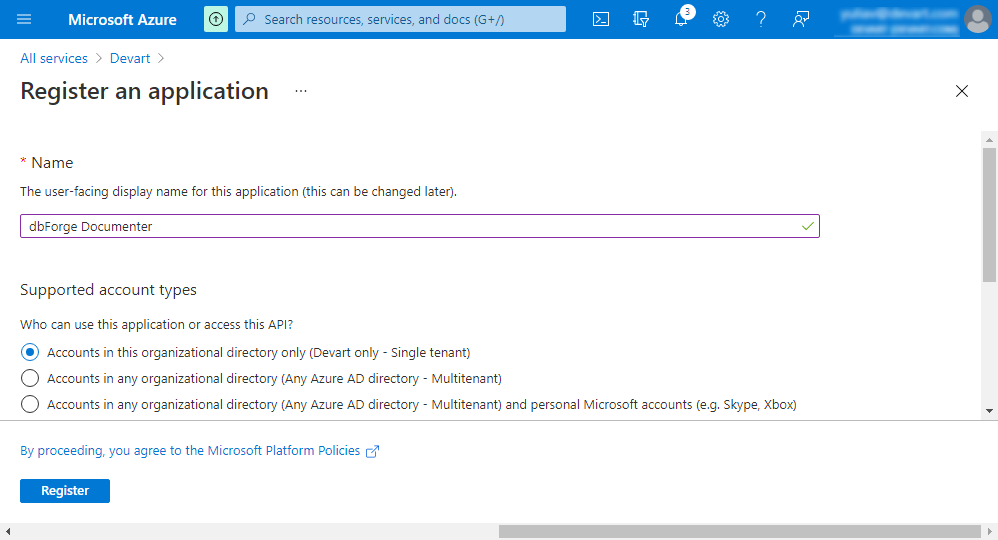
Note
After dbForge Documenter has been registered as an application, the application ID is generated automatically. It is a unique and unchangeable identifier for dbForge Documenter for SQL Server. You need to copy and save it to connect dbForge Documenter for SQL Server to the Azure database.
4. On the page that opens, click Add a Redirect URI.
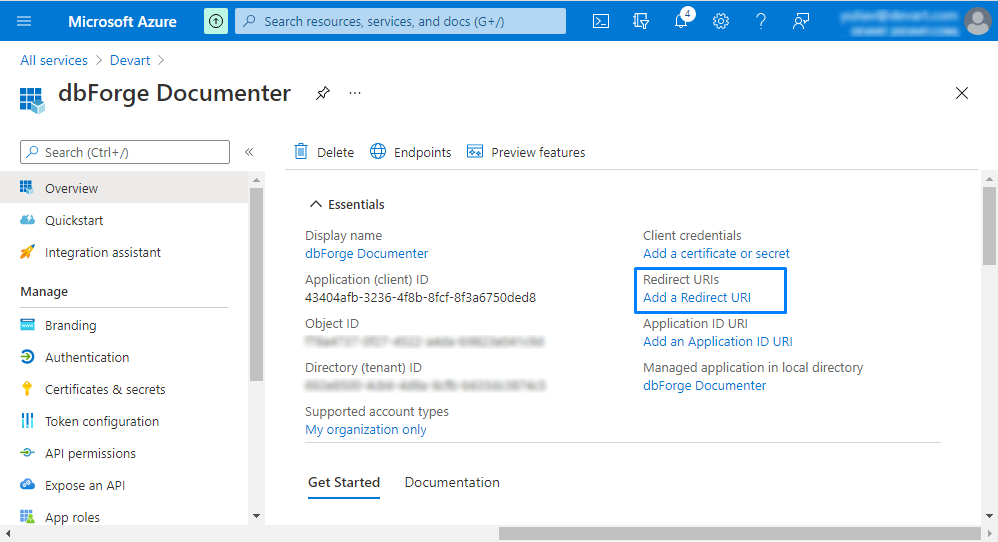
5. On the dbForge Documenter > Authentication page, click Add a platform and then click Mobile and desktop applications.
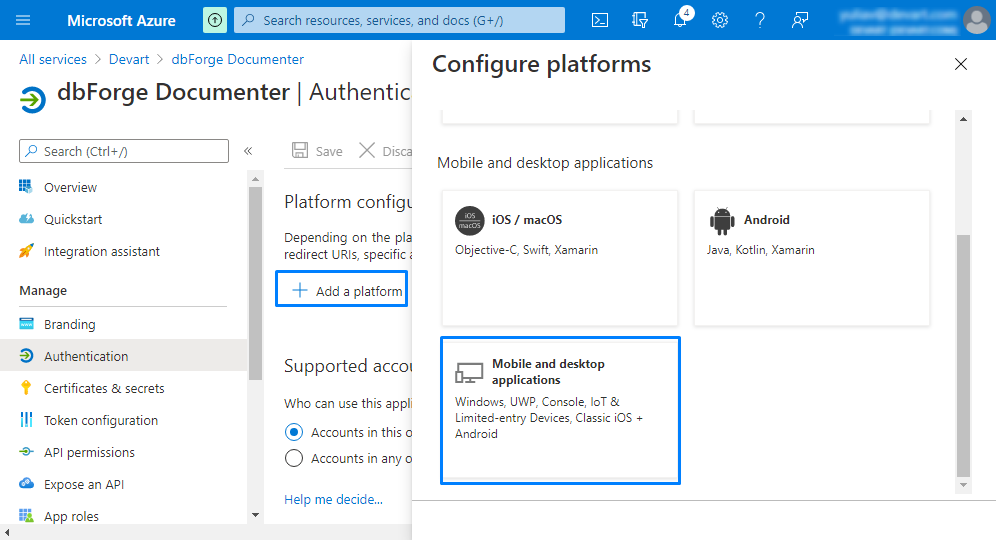
6. In the Configure Desktop + Devices window, select https://login.microsoftonline.com/common/oauth2/nativeclient as a redirect URI and click Configure.
7. On the Authentication page, switch to the Advanced settings section, turn the toggle switch next to Allow public client flows to Yes, and then click Save.
8. In the Azure portal, click API permissions and then click Add a permission.
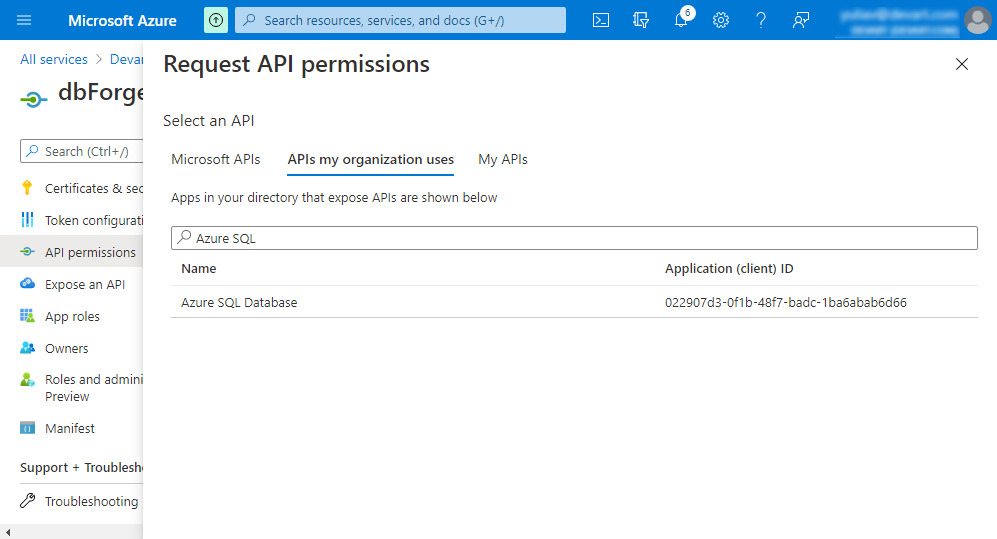
9. In the Request API permissions window that opens, switch to the APIs my organization uses tab and start typing Azure SQL Database in the Search field.
10. From the drop-down list, select Azure SQL Database.
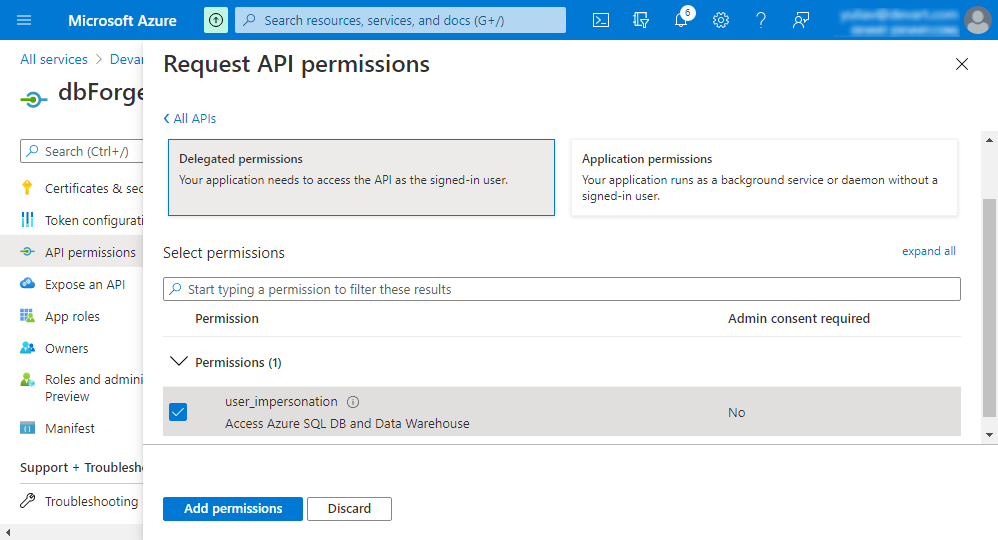
11. Click Delegated permissions, select the user_impersonation checkbox, and then click Add permissions.
Download dbForge SQL documentation generator and try it absolutely free for 30 days!