 SecureBridge Components
SecureBridge ComponentsTScSSLSecurityOptions.IgnoreServerCertificateInsecurity
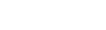
property IgnoreServerCertificateInsecurity: boolean; default False;
Description
Determines whether a server certificate signature security will be checked during the TLS/SSL handshake when starting a new session.
Set IgnoreServerCertificateInsecurity to True, in order for the client to ignore the certificate signature security. Set IgnoreServerCertificateInsecurity to False, in order for the client to check the certificate signature security.
In case if a hash algorithm for signing the certificate is set to one of following algorithms: [haNone, haSHA1, haMD5, haMD4, haMD2], - signature is considered insecured, and therefore, the TLS server is considered invalid, and the session is closed.
The default value is False.
See also
IgnoreServerCertificateConstraints
IgnoreServerCertificateValidity
TScSSLClient.ClientHelloExtensions