 SecureBridge Components
SecureBridge ComponentsSSH-tunnel principles
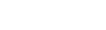
SSH (Secure Shell) is the protocol for secure access to remote computers over insecure communication channels.
The general chart of computer ties when connecting through the SSH tunnel is presented below:
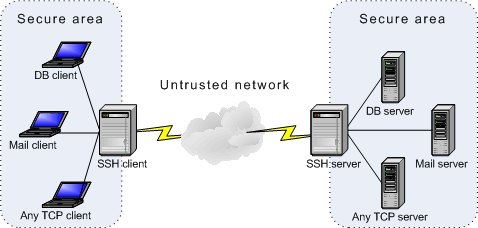
C1, C2, ..., Cn - computers from the client side of the SSH tunnel.
S1, S2, ..., Sn - computers from the server side of the SSH tunnel. This can be a database server, http server, or just other client computers.
This connection method provides the secure connection between SSH client and SSH server that can go through insecure communication channels, like Internet.
Connections between Si and SSH server, and between SSH client and Ci are insecure, therefore they should go through secure communication channels. In the confluent case, Si and SSH server can be located on the same computer. The same is related to the SSH client and Ci.
The principle of working of the SSH connections is described below. The SSH server listens to the specified TCP/IP port. When SSH client tries to connect to this port, the SSH server authenticates the client. If the authentication passes, the connection is established. Then the client should create connections to Si objects. The SSH client sends an inquiry to establish necessary connection to SSH server, and the server establishes it.
Also you can work in port forwarding mode. Port forwarding, or tunneling, is a way to forward otherwise insecure TCP traffic through SSH Secure Shell. There are two kinds of port forwarding: Local port forwarding and Remote port-forwarding.
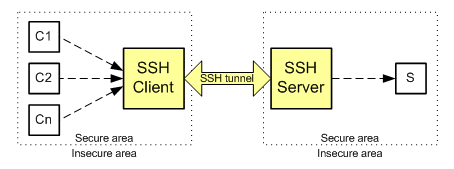
In this mode the SSH client listens the specified port. If a Ci computer from the client side of the tunnel needs to connect to the server S, Ci should connect to SSH client and the SSH client creates the secure channel to S via the SSH server.
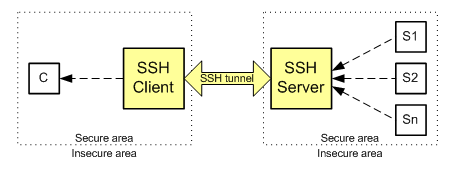
In this mode SSH client sends a request to SSH to listen a specific port. If a Si computer from the server side wants to connect to the client C, Si should connect to the SSH server through the specified port, and the SSH server will create a secure channel to C through the SSH client.